C23C20
False-Accident Cyberattacks on Traffic Flow Stability Microscopic Vehicle Interactions
in Connected Vehicle-Enabled Traffic System
Investigator(s):
- Guohui Zhang, University of Hawai’i at Manoa, ORCID # 0000-0001-5194-9222 (PI)
Project Description:
Cyber security issues in the vehicular network have emerged as serious concerns for successful deployment of CV systems. In the existing literature, the analysis of the cyber security impacts has been primarily focused from the computer science perspectives investigating potential attacking scenarios and countermeasures through network security strategies. One key concern towards the decision is the cyber security issues in the Vehicle Ad Hoc Network (VANET). Cyber-attacks in VANET have potentially catastrophic consequences such as property damages, human injuries, or even fatalities. The security of VANETs has been paid more attention to for the reasons that potential attacks may lead to catastrophic results, including the loss of lives and properties, and impede its wide application. Therefore, the security issues of VANETs are studied in many research projects. Due to the massive impact of cyber-attacks, there is an urgent research need to enhance CV-enabled traffic control system cybersecurity and prevent accident occurrence. In this project, we propose to investigate traffic impacts of cyber-attacks considering real-world driver behavior, especially the “built-in” safety redundancy of the visual verification by drivers or autonomous driving system. In order to secure the VANETs, potential attacks should be investigated first. In the proposed project, a car-following model is developed to describe the interaction between two successive vehicles and has been the foundation of microscopic traffic simulation. Car-following models can be generalized as a function of vehicle control variables such as acceleration or velocity with respect to vehicle state variables such as vehicle spacing, velocity difference in the previous time interval. Traffic flow stability can be analyzed through linear stability theories when the model has proper analytic characteristics. The stability can also be analyzed through numerical simulation when the analytical stability condition is difficult to derive. Then, a ring-road numerical stability analysis method is proposed to evaluate the impacts of cyber-attacks on general traffic and vehicle interactions. Figure 1 illustrates our preliminary study results in terms of traffic flow stability analysis for different false-accident attack durations under free flow condition. The research results will be helpful to enhance our understanding of CV operation and its Cyber-attack response.
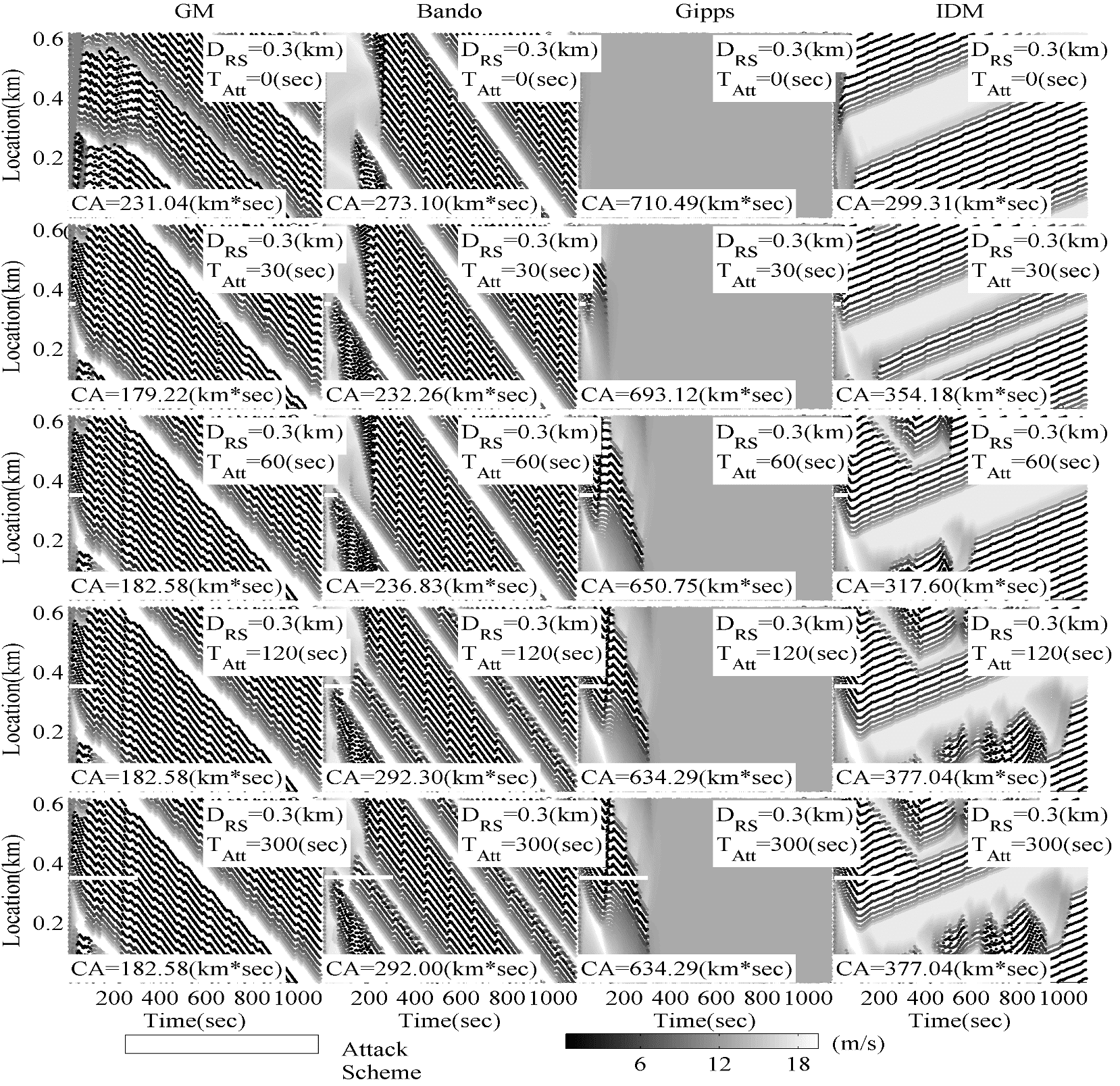
Figure 1 Prelimiary traffic flow stability analysis for false-accident attack durations
in free flow condition.
The major research objectives of this project include:
- Develop and investigate traffic impacts of cyber-attacks considering real-world driver behavior.
- Investigate the impact of “false-accident” attacks on the stability of traffic flow assuming a vehicle sends out a false accident alert to its surrounding vehicle through CV-enabled network and has considered an attacking scenario that has catastrophic effects.
- Analyze traffic flow stability based on widely-used numerical linear stability examination methods on a ring road