C23C11
Transfer and Semi-supervised Learning for Cybersecurity in Transportation
Investigator(s):
Arlei Silva, Rice University, ORCID # 0000-0003-1792-0076 (PI)
Project Description:
This project is focused on intrusion detection for transportation cybersecurity. Given a sequence of network communication flows between pairs of network entities (IP numbers), the goal is to detect a subset of flows that represent potential network intrusions. We will focus on graph machine learning algorithms that learn structural patterns in the data for intrusion detection. However, due to the unavailability of labeled data indicating intrusions in transportation domains, we will propose semi-supervised and transfer learning models for intrusion detection. Semi-supervised learning reduces the dependency of the model on large amounts of labeled data by leveraging unlabeled data. Moreover, transfer learning will enable labeled data from other domains to be used to detect intrusions in transportation systems. We summarize the major objectives of this project as follows:
We summarize the major objectives of this project as follows :
- Develop graph-based intrusion detection models using GNNs.
- Introduce semi-supervised and transfer-learning approaches for intrusion detection.
- Evaluate proposed solutions using datasets from transportation domains.
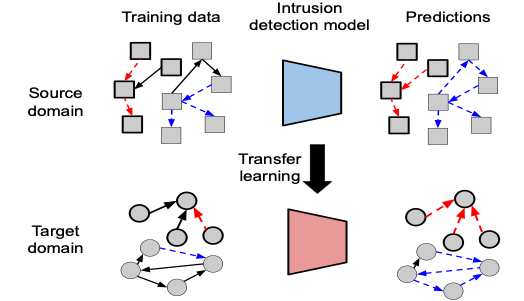
Figure 1. Transfer learning for intrusion detection
Figure 1 illustrates our transfer learning approach for intrusion detection. Figure 2 shows preliminary results for our transfer learning approach using the CIC-IDS2017 dataset as source (labeled) and the CIC-IDS2018 dataset as target (scarce labels). We show 2D representations learned by our model for communication flows that are both benign and attacks (DDoS). False Positives (FP) and False Negatives (FN) are also shown. The results show how transfer learning enables the discovery of intrusions in the target dataset.