C23C05
Blockchain-Based Defense for ML/DL Models and IoV Cyber Attacks
Investigator(s):
Dr. Zhu Han, University of Houston, ORCID # 0000-0002-6606-5822 (PI)
Project Description:
The project team will explore the following research questions.
- How the knowledge learned across various projects can be aggregated to facilitate IoVs collaborative learning for improved intelligence via an FL framework?
- How blockchain can be integrated with the FL framework to ensure privacy and security?
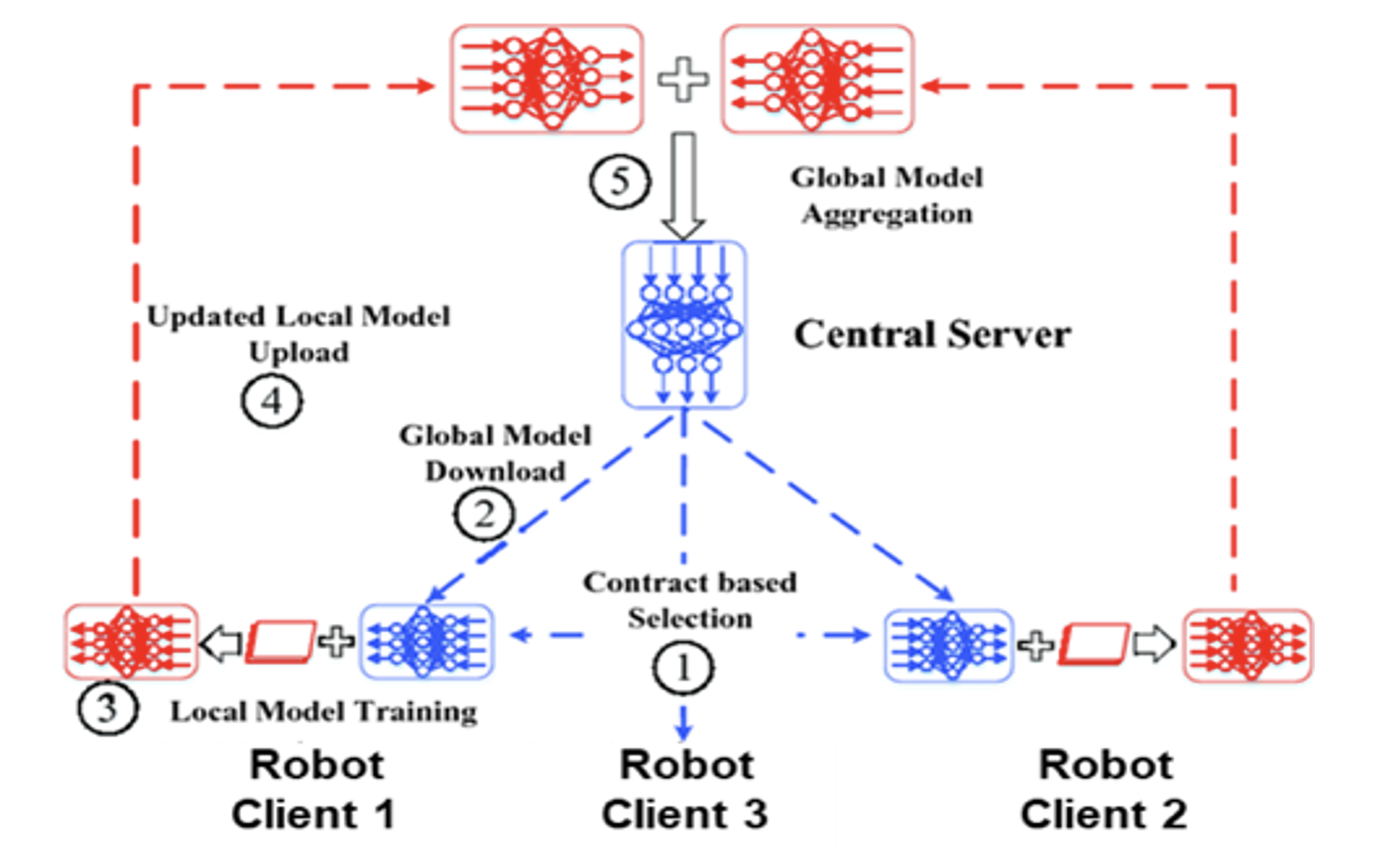
Figure 1 - Proposed selective model aggregation in FL
The general framework of FL consists of the following components (Figure 1): Central Server plays a core role in the procedure of FL. IoV Clients are equipped with a set of built-in sensors, such as cameras, GPS, tachographs, and lateral acceleration sensors, and accommodate storage space, computation, and communication resources. The built-in sensors are used to capture sensing data that may be preprocessed for data augment. After that, the preprocessed data are classified and labeled by our scene understanding methods and are cached in IoV clients. After receiving a request from a central server, IoV clients separately train local deep learning models with their local sensory. IoV clients send updated local deep-learning models to the central server for model aggregation.
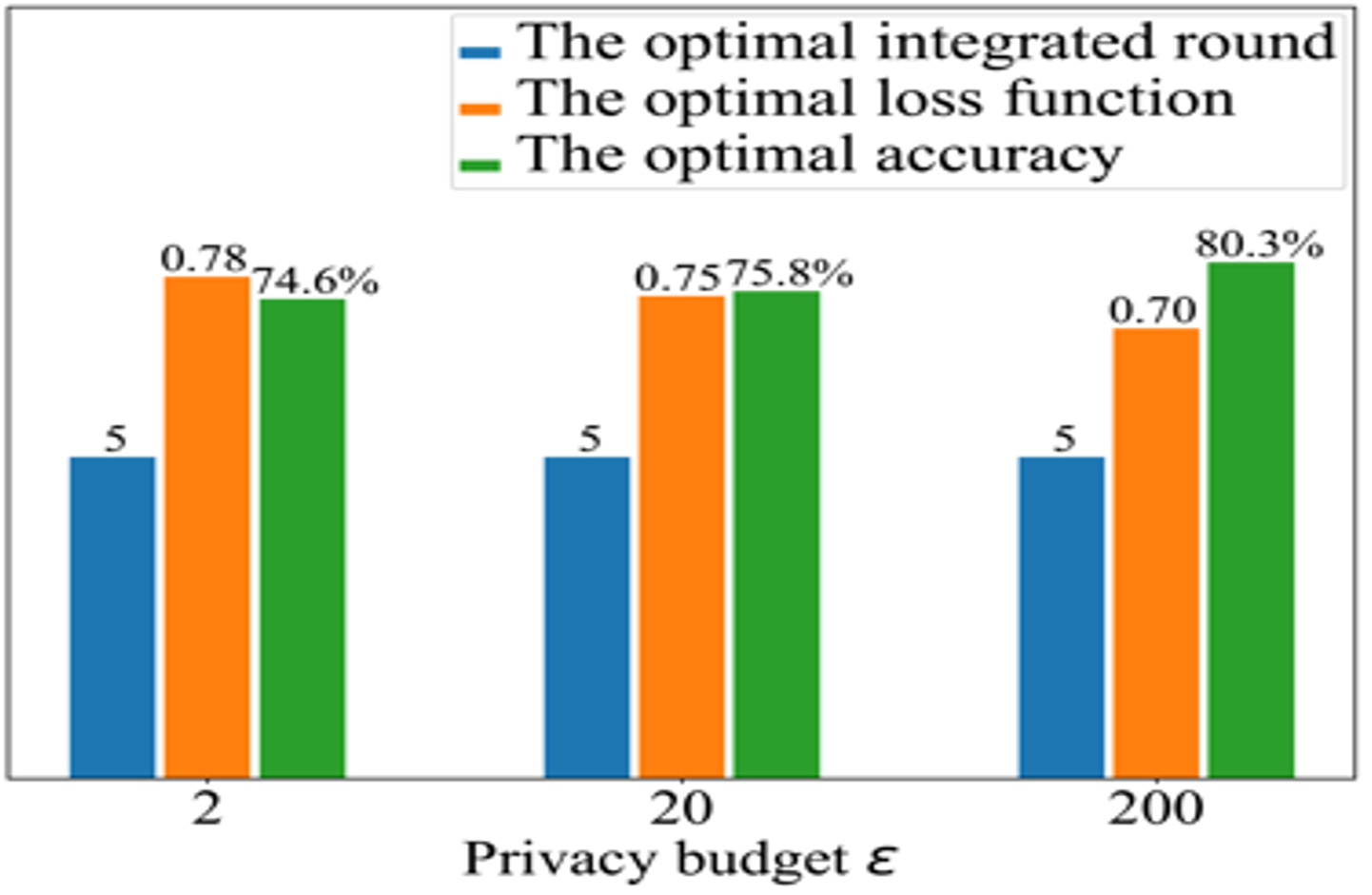
Figure 2 - Team’s solution is leading positive outcome with preliminary results for
BLADE-FL.
FL will randomly assign some IoV clients to perform tasks of training the local models. The selected IoV clients have diverse data quality and computation capabilities, which reduces the accuracy and efficiency of model aggregation. To cope with the above dilemma, we will propose a selective model aggregation approach with five steps (Fig. 1) Contract-based selection: the central server initializes a global deep learning model. Based on the historical records of IoV clients, the central server evaluates their data quality and computation capability. The central server designs two-dimensional contract items for IoV clients. Figure 2 shows the team’s solution is leading to a positive outcome with preliminary results for BLADE-FL.