C23C10
Human-AI Teams for Cybersecurity in Transportation
Investigator(s):
Christopher Jermaine, Rice University, ORCID # 0009-0001-5458-9370 (PI)
Project Description:
This project is focused on online intrusion detection for cybersecurity. The main goal is to develop models and algorithms to support the collaboration between humans and AI for the rapid discovery of cybersecurity attacks based on data streams (sequences of communication events). This online version of the problem is more challenging than the traditional batch setting where the model has access to the entire dataset. Addressing this problem will require the design of efficient and interpretable data analytics tools and models for incorporating human feedback into the intrusion detection model to improve the patterns discovered iteratively. Recent advances in explainable AI will be leveraged to provide cybersecurity experts with insights into why a given communication pattern is a potential intrusion. The proposed approaches will be compared against existing alternatives, including those that do not incorporate human feedback, in terms of accuracy and detection time.
We summarize the major objectives of this project as follows :
- Design rapid-response interpretable data analytics models for potential cyber-attacks
- Design human-in-the-loop approaches for cyber-attack detection
- Evaluate human-AI cybersecurity collaborations on a representative set of attacks.
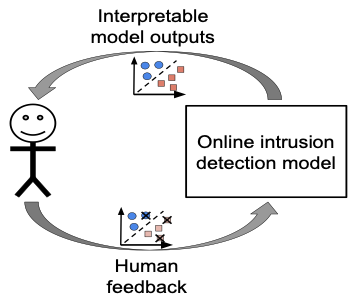
Figure 1 Human-AI teams for cybersecurity.
Figure 1 illustrates our proposed approach for human-AI collaborations in cybersecurity. This project will engage in transformative research by developing new machine-learning models and data analytics tools. The team will develop novel efficient data analytics approaches for the detection of cyber threats in transportation systems. These algorithms will process heterogeneous sources of data, including communication and user activity, in a streaming fashion. We will focus on anomaly detection schemes to detect unusual activity in the system but will also consider supervised approaches. Next, we will introduce interpretable models to support cybersecurity experts in understanding different types of attacks. We will consider explanations tailored for different levels of expertise (e.g., based on the vulnerability exploited by the attack and their impact on the transportation system). Finally, we will investigate how to extend the proposed analytics and explanations to human-in-the-loop settings. The idea is to incorporate user feedback in order to tailor the system to the needs of a variety of users.